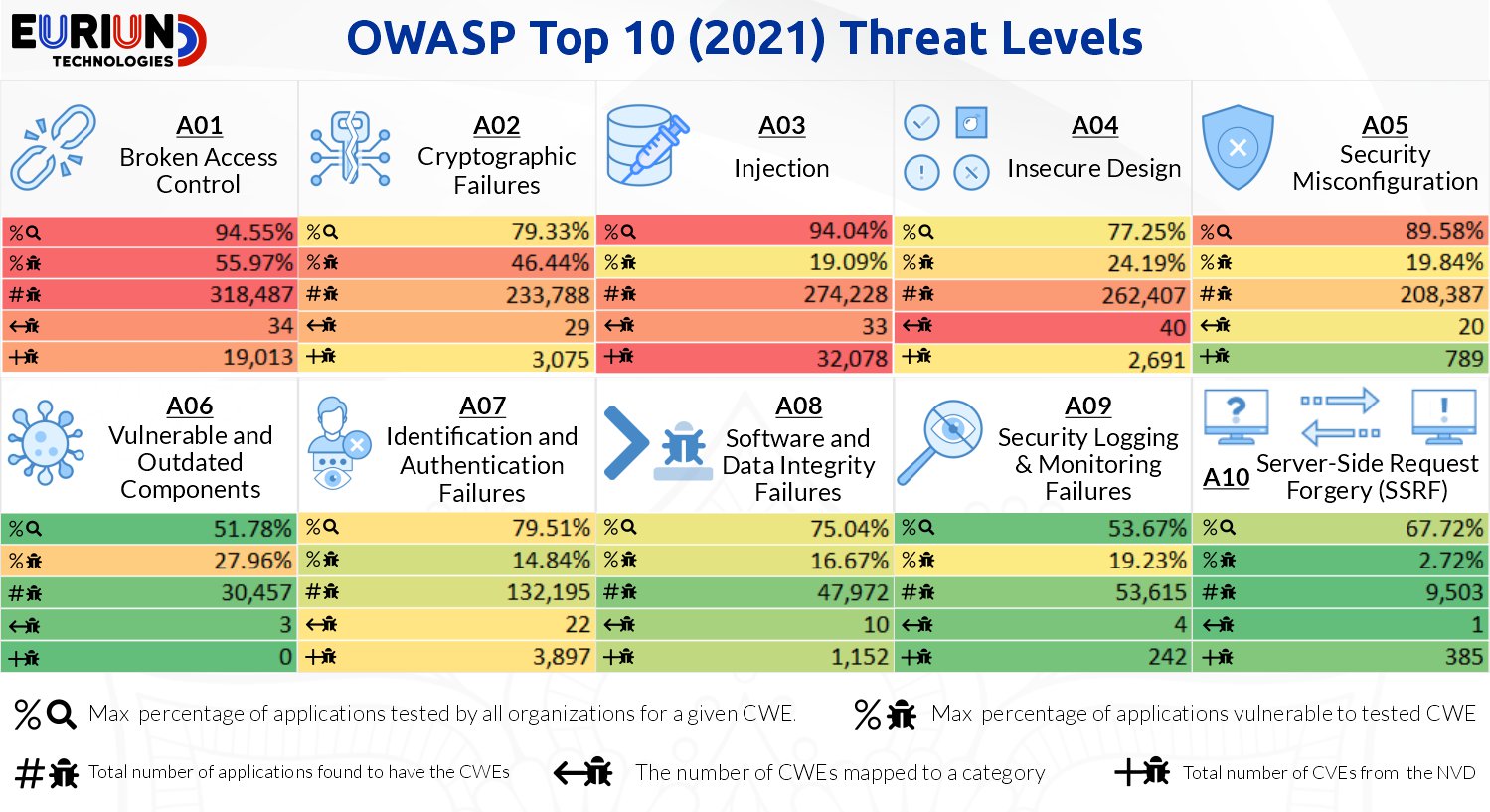

A01 – Broken Access Control
Restrictions on what authenticated users are allowed to do are often not properly validated. Access control policies should enforce rules to ensure users cannot act outside of their intended permissions e.g. URL modification to access hidden pages.

A02 – Cryptographic Failures
Sensitive data in transit and at rest run the risk of unauthorized interception and/or modification when not properly protected. Encryption with secure protocols should be enforced for all sensitive data in transit and at rest where applicable.

A03 – Injection
Injection flaws such as SQL, OS command, LDAP, JSON and XML injection occurs when untrusted user-supplied data is not validated, filtered, sanitized or encoded by the application which can lead to an attacker accessing data without proper authorization.

A04 – Insecure Design
Insecure Design highlights the risks related to application design and architectural flaws. Recommendations involve the use of threat modeling (https://owasp.org/www-community/Threat_Modeling_Process) and secure application development lifecycle (https://owaspsamm.org/).

A05 – Security Misconfiguration
Security misconfiguration is most commonly as a result of insecure or incomplete default configurations. Operating systems, frameworks, libraries, and applications must be securely configured, updated and patched in a timely fashion.

A06 – Vulnerable and Outdated Components
Libraries, frameworks, and other software modules, run with the same privileges as their applications. If a vulnerable component is exploited, such an attack can facilitate critical data loss or a server hijack.

A07 – Identification and Authentication Failures
Confirmation of the user’s identity, authentication, and session management are critical to protect against authentication-related attacks. Additional security features like multi-factor authentication can help prevent automated attacks such as credential stuffing and brute force.
A08 – Software and Data Integrity Failures
Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations. Plugins, libraries, or modules downloaded/used from external sources, repositories, and content delivery networks (CDNs) must enforce sufficient integrity verification.

A09 – Security Logging and Monitoring Failures
Security logging and monitoring can help detect, escalate, and respond to potential/active breaches. A combination of solutions such as a Security Information and Event Management (SIEM), Web Application Firewall (WAF) and Intrusion Detection & Prevention Systems (ID&PS) can effectively monitor, alert and/or prevent potential attacks.

A10 – Server-Side Request Forgery (SSRF)
SSRF flaws occur whenever a web application is requesting a remote resource without validating the user-supplied entry. It allows an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall, VPN, or another type of network access control list (ACL).
