Zero Trust Security (Identity, Device, Network, OS, Database, Application, Data)
The implementation of a Zero Trust Security Model to cover all enterprise assets, resources (end users, applications and other non-human entities that request information) can help prevent unauthorized access to data and services and enforce granular access control policies by implementing continuous evaluation of access rights.
- An optimal level of Security for Digital Identities should include enrollment, authentication, authorization and continuous validation of access rights.
- An optimal level of Security for Devices should include authentication factors, access validation and continuous device security monitoring.
- An optimal level of Security for Network and Application Data should include traffic and data encryption respectively.

Security Reference: https://www.euriun.com/zero-trust-security/
Security Assessment and Remediation Automation
Automation of security operations can help improve the reliability of deploying, configuring, updating, and monitoring of security-related information using well established standards, frameworks and/or guidelines.
Security Automation solutions should basically include:
- Tracking compliance using benchmarks and scoring systems e.g. Common Vulnerability Scoring System (CVSS)
The ability to integrate and be interoperable with multiple sources and products. - Support for compliance and reports in line with applicable federal laws, executive orders, directives, policies, regulations, standards, and guidelines.
- Support for data consolidation into Security Information and Event Management (SIEM), and Data Analytics solutions.
Security References:
https://azure.microsoft.com/en-us/services/automation/
https://aws.amazon.com/lambda/it-automation/
https://www.redhat.com/en/technologies/management/ansible
https://www.jenkins.io
https://puppet.com
https://www.chef.io
Sensitive Data Classification and Protection
Data is considered sensitive if its compromise could directly or indirectly cause financial, reputational or personal harm to its owner or anyone associated with it.
Enterprises that transmits and/or stores sensitive data (Passwords, Debit/Credit card numbers, CVVs, etc.) should ensure the data is secured using a strong encryption algorithm.
Data Security can be applied at different levels such as:
- The application level (Encryption)
- The database level (Hashing, Encryption, Masking)
- The filesystem level (Encryption)
- The hardware level (Encryption)
Data Classification can be implemented according to the importance of its content and based on guidelines such as:
- Sensitivity (Sensitive vs. Non-Sensitive)
- Frequency (Frequently accessed vs. Non-frequently accessed)
- Environment (Production vs. Development vs. Testing vs. Staging)
Security Reference: https://cheatsheetseries.owasp.org/cheatsheets/Cryptographic_Storage_Cheat_Sheet.html
Centralized Management of Security Information and Events
Logs are critical in identifying anomalies in systems and applications by recording events such as changes to systems or accounts. Consider using solutions that can aggregate or centralize logs to enable easy monitoring and visualization.
Log management includes log collection/aggregation, secure storage, normalization, event analysis, reporting, and notification/alert generation.
Security Reference: https://audilitics.com/server/central-log-server-siem-audit/
Risk Management
Organizations can manage information security risk using the NIST Risk Management Framework which provides a series of processes and tasks that integrates security and risk management activities into the data, system and services life cycle.
The Risk Management strategy typically involves organizations establishing the context for risk-based decisions (framing), assessing, responding to, and monitoring risks.
The Risk Management execution process involves seven steps essential for the successful execution of the Risk Management Framework which includes:
- Preparing the context and priorities for managing security and privacy risk.
- Categorizing the system and the information processed, stored, and transmitted by the system based on an analysis of the impact of loss.
- Selecting an initial set of controls for the system and customizing the controls as needed to reduce risk to an acceptable level based on an assessment of risk.
- Implementing the controls and describing how the controls are employed within the system and its environment of operation.
- Assessing the controls to determine if the controls are implemented correctly, operating as intended, and producing the desired outcomes with respect to satisfying the security and privacy requirements.
- Authorizing the system or common controls based on a determination that the risk to organizational operations and assets, individuals, and other organizations is acceptable.
- Monitoring the system and the associated controls on an ongoing basis to include assessing control effectiveness, documenting changes to the system and environment of operation, conducting risk assessments and impact analysis, and reporting the security and privacy posture of the system.
Security Reference: https://audilitics.com/security/risk-management-audit/
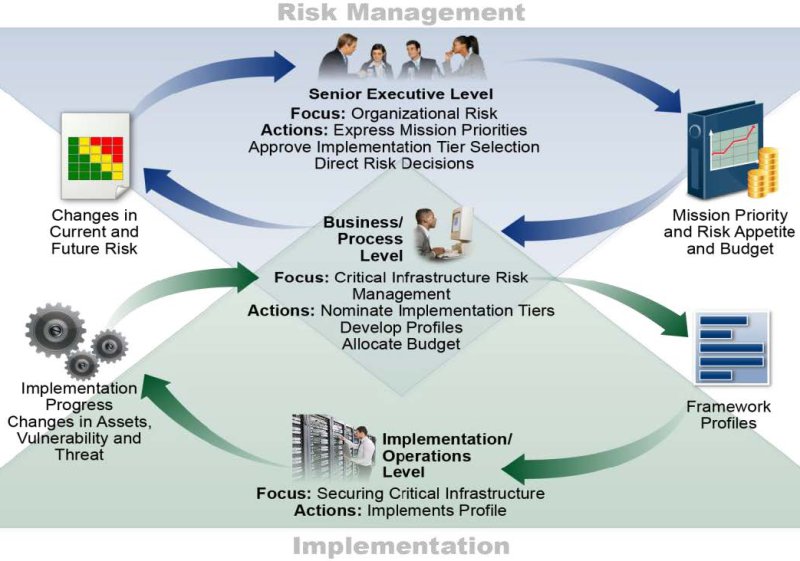
High Level Process flow of collaboration to address Cybersecurity Risk Management - NIST