NIST Cybersecurity Framework 2.0 - Overview and Reference Guide
The NIST Cybersecurity Framework (CSF) 2.0 provides an updated guidance for organizations on how to understand, assess, prioritize, communicate and manage cybersecurity risks alongside other risks of the enterprise, including financial, privacy, supply chain, reputational, technological, or physical risks.
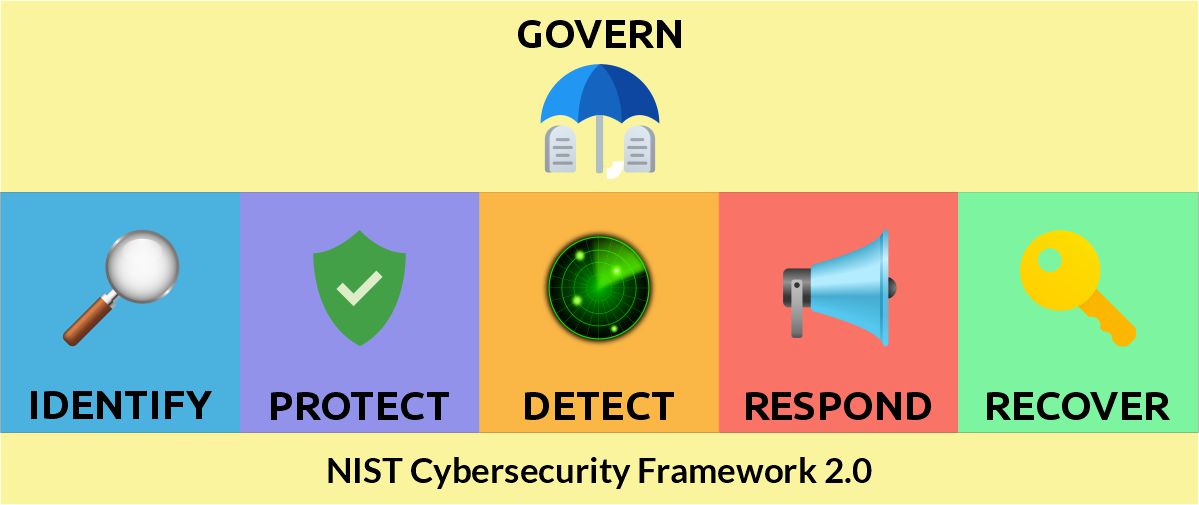
The core of the Cybersecurity Framework contains a set of six Functions (Govern, Identify, Protect, Detect, Respond, and Recover), Categories (Guidance), Subcategories (Recommendations), Implementation Examples (Procedures) and Applicable Risks that provides a comprehensive guideline for managing cybersecurity risk.
The Functions, Categories, and Subcategories apply to all ICT used by an organization, including Information Technology (IT), the Internet of Things (IoT), and Operational Technology (OT). They also apply to all types of technology environments, including cloud, mobile, and artificial intelligence systems.

GOVERN
The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
• Understand and assess specific cybersecurity needs.
• Develop a tailored cybersecurity risk strategy.
• Establish defined risk management policies.
• Develop and communicate organizational cybersecurity practices.
• Establish and monitor cybersecurity supply chain risk management.
• Implement continuous oversight and checkpoints.

IDENTIFY
The organization’s current cybersecurity risks are understood.
- Identify critical business processes and assets.
- Maintain inventories of hardware, software, services, and systems.
- Document information flows.
- Identify threats, vulnerabilities, and risk to assets.
- Lessons learned are used to identify improvements.

PROTECT
Safeguards to manage the organization’s cybersecurity risks are implemented.
- Manage and track physical access to facilities and devices
- Protect and monitor your devices.
- Protect sensitive data.
- Manage and maintain software.
- Conduct regular backups.
- Train users.

DETECT
Potential cybersecurity attacks and compromises are discovered and analyzed.
- Identify critical business processes and assets.
- Maintain inventories of hardware, software, services, and systems.
- Document information flows.
- Identify threats, vulnerabilities, and risk to assets.
- Lessons learned are used to identify improvements.

RESPOND
Actions regarding a detected cybersecurity incident are taken.
- Execute an incident response plan once an incident is declared, in coordination with relevant third parties.
- Categorize and prioritize incidents and escalate or elevate as required.
- Collect incident data and preserve its integrity and provenance.
- Contain and eradicate incidents.
- Notify internal and external stakeholders of any incidents and share incident information with them in line with your organization policies.

RECOVER
Assets and operations affected by a cybersecurity incident are restored.
- Understand your organization’s roles and responsibilities.
- Execute your recovery plan.
- Communicate with internal and external stakeholders.
- Verify your work.
| wdt_ID | S/N | Function | Category | Category Description (Guidance) | SID | Subcategory (Recommendations) | Implementation (Procedure) | Risk Applicability | References | Changelog |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 | GOVERN | Organizational Context | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood | GV.OC-01 | The organizational mission is understood and informs cybersecurity risk management | Ex1: Share the organization's mission (e.g., through vision and mission statements, marketing, and service strategies) to provide a basis for identifying risks that may impede that mission | 1st Party Risk | CRI Profile v2.0: GV.OC-01 CRI Profile v2.0: GV.OC-01.01 SP 800-221A: GV.CT-5 SP 800-221A: GV.CT-3 CSF v1.1: ID.BE-2 CSF v1.1: ID.BE-3 | formerly ID.BE-02, ID.BE-03 |
| 2 | 2 | GOVERN | Organizational Context | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood | GV.OC-02 | Internal and external stakeholders are understood, and their needs and expectations regarding cybersecurity risk management are understood and considered | Ex1: Identify relevant internal stakeholders and their cybersecurity-related expectations (e.g., performance and risk expectations of officers, directors, and advisors; cultural expectations of employees) Ex2: Identify relevant external stakeholders and their cybersecurity-related expectations (e.g., privacy expectations of customers, business expectations of partnerships, compliance expectations of regulators, ethics expectations of society) | 1st & 3rd Party Risk | SP 800-218: PO.2.1 CRI Profile v2.0: GV.OC-02 CRI Profile v2.0: GV.OC-02.01 CRI Profile v2.0: GV.OC-02.02 CRI Profile v2.0: GV.OC-02.03 SP 800-221A: GV.OV-2 SP 800-221A: GV.CT-2 SP 800-221A: GV.CT-3 CSF v1.1: ID.SC-2 CSF v1.1: ID.GV-2 | |
| 3 | 3 | GOVERN | Organizational Context | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood | GV.OC-03 | Legal, regulatory, and contractual requirements regarding cybersecurity - including privacy and civil liberties obligations - are understood and managed | Ex1: Determine a process to track and manage legal and regulatory requirements regarding protection of individuals' information (e.g., Health Insurance Portability and Accountability Act, California Consumer Privacy Act, General Data Protection Regulation) Ex2: Determine a process to track and manage contractual requirements for cybersecurity management of supplier, customer, and partner information Ex3: Align the organization's cybersecurity strategy with legal, regulatory, and contractual requirements | 1st & 3rd Party Risk | SP 800-218: PO.1.1 SP 800-218: PO.1.2 CRI Profile v2.0: GV.OC-03 CRI Profile v2.0: GV.OC-03.01 CRI Profile v2.0: GV.OC-03.02 CSF v1.1: ID.GV-3 | formerly ID.GV-03 |
| 4 | 4 | GOVERN | Organizational Context | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood | GV.OC-04 | Critical objectives, capabilities, and services that stakeholders depend on or expect from the organization are understood and communicated | Ex1: Establish criteria for determining the criticality of capabilities and services as viewed by internal and external stakeholders Ex2: Determine (e.g., from a business impact analysis) assets and business operations that are vital to achieving mission objectives and the potential impact of a loss (or partial loss) of such operations Ex3: Establish and communicate resilience objectives (e.g., recovery time objectives) for delivering critical capabilities and services in various operating states (e.g., under attack, during recovery, normal operation) | 1st & 3rd Party Risk | CRI Profile v2.0: GV.OC-04 CRI Profile v2.0: GV.OC-04.01 CRI Profile v2.0: GV.OC-04.02 CRI Profile v2.0: GV.OC-04.03 CRI Profile v2.0: GV.OC-04.04 SP 800-221A: MA.RI-1 CSF v1.1: ID.BE-4 CSF v1.1: ID.BE-5 | formerly ID.BE-04, ID.BE-05 |
| 5 | 5 | GOVERN | Organizational Context | The circumstances - mission, stakeholder expectations, dependencies, and legal, regulatory, and contractual requirements - surrounding the organization's cybersecurity risk management decisions are understood | GV.OC-05 | Outcomes, capabilities, and services that the organization depends on are understood and communicated | Ex1: Create an inventory of the organization's dependencies on external resources (e.g., facilities, cloud-based hosting providers) and their relationships to organizational assets and business functions Ex2: Identify and document external dependencies that are potential points of failure for the organization's critical capabilities and services, and share that information with appropriate personnel | 3rd Party Risk | CRI Profile v2.0: GV.OC-05 CRI Profile v2.0: GV.OC-05.01 CRI Profile v2.0: GV.OC-05.02 CRI Profile v2.0: GV.OC-05.03 CRI Profile v2.0: GV.OC-05.04 SP 800-221A: GV.CT-5 SP 800-221A: MA.RI-1 CSF v1.1: ID.BE-1 CSF v1.1: ID.BE-4 | formerly ID.BE-01, ID.BE-04 |
| 6 | 6 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-01 | Risk management objectives are established and agreed to by organizational stakeholders | Ex1: Update near-term and long-term cybersecurity risk management objectives as part of annual strategic planning and when major changes occur Ex2: Establish measurable objectives for cybersecurity risk management (e.g., manage the quality of user training, ensure adequate risk protection for industrial control systems) Ex3: Senior leaders agree about cybersecurity objectives and use them for measuring and managing risk and performance | 1st Party Risk | CRI Profile v2.0: GV.RM-01 CRI Profile v2.0: GV.RM-01.01 CRI Profile v2.0: GV.RM-01.02 CRI Profile v2.0: GV.RM-01.03 CRI Profile v2.0: GV.RM-01.04 CRI Profile v2.0: GV.RM-01.05 SP 800-221A: GV.RR-2 CSF v1.1: ID.RM-1 | formerly ID.RM-01 |
| 7 | 7 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-02 | Risk appetite and risk tolerance statements are established, communicated, and maintained | Ex1: Determine and communicate risk appetite statements that convey expectations about the appropriate level of risk for the organization Ex2: Translate risk appetite statements into specific, measurable, and broadly understandable risk tolerance statements Ex3: Refine organizational objectives and risk appetite periodically based on known risk exposure and residual risk | 1st & 3rd Party Risk | CRI Profile v2.0: GV.RM-02 CRI Profile v2.0: GV.RM-02.01 CRI Profile v2.0: GV.RM-02.02 CRI Profile v2.0: GV.RM-02.03 SP 800-221A: GV.BE-1 SP 800-221A: GV.BE-3 CSF v1.1: ID.RM-2 CSF v1.1: ID.RM-3 | formerly ID.RM-02, ID.RM-03 |
| 8 | 8 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-03 | Cybersecurity risk management activities and outcomes are included in enterprise risk management processes | Ex1: Aggregate and manage cybersecurity risks alongside other enterprise risks (e.g., compliance, financial, operational, regulatory, reputational, safety) Ex2: Include cybersecurity risk managers in enterprise risk management planning Ex3: Establish criteria for escalating cybersecurity risks within enterprise risk management | 1st Party Risk | CRI Profile v2.0: GV.RM-03 CRI Profile v2.0: GV.RM-03.01 CRI Profile v2.0: GV.RM-03.02 CRI Profile v2.0: GV.RM-03.03 CRI Profile v2.0: GV.RM-03.04 SP 800-221A: GV.PO-2 SP 800-221A: GV.PO-3 CSF v1.1: ID.GV-4 | formerly ID.GV-04 |
| 9 | 9 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-04 | Strategic direction that describes appropriate risk response options is established and communicated | Ex1: Specify criteria for accepting and avoiding cybersecurity risk for various classifications of data Ex2: Determine whether to purchase cybersecurity insurance Ex3: Document conditions under which shared responsibility models are acceptable (e.g., outsourcing certain cybersecurity functions, having a third party perform financial transactions on behalf of the organization, using public cloud-based services) | 1st Party Risk | CRI Profile v2.0: GV.RM-04 CRI Profile v2.0: GV.RM-04.01 SP 800-221A: GV.BE-1 CSF v1.1: ID.RM-2 | |
| 10 | 10 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-05 | Lines of communication across the organization are established for cybersecurity risks, including risks from suppliers and other third parties | Ex1: Determine how to update senior executives, directors, and management on the organization's cybersecurity posture at agreed-upon intervals Ex2: Identify how all departments across the organization - such as management, operations, internal auditors, legal, acquisition, physical security, and HR - will communicate with each other about cybersecurity risks | 1st & 3rd Party Risk | CRI Profile v2.0: GV.RM-05 CRI Profile v2.0: GV.RM-05.01 CRI Profile v2.0: GV.RM-05.02 SP 800-221A: GV.PO-1 CSF v1.1: ID.SC-1 | |
| 11 | 11 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-06 | A standardized method for calculating, documenting, categorizing, and prioritizing cybersecurity risks is established and communicated | Ex1: Establish criteria for using a quantitative approach to cybersecurity risk analysis, and specify probability and exposure formulas Ex2: Create and use templates (e.g., a risk register) to document cybersecurity risk information (e.g., risk description, exposure, treatment, and ownership) Ex3: Establish criteria for risk prioritization at the appropriate levels within the enterprise Ex4: Use a consistent list of risk categories to support integrating, aggregating, and comparing cybersecurity risks | 1st Party Risk | CRI Profile v2.0: GV.RM-06 CRI Profile v2.0: GV.RM-06.01 SP 800-221A: GV.RR-2 CSF v1.1: ID.RM-1 | |
| 12 | 12 | GOVERN | Risk Management Strategy | The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions | GV.RM-07 | Strategic opportunities (i.e., positive risks) are characterized and are included in organizational cybersecurity risk discussions | Ex1: Define and communicate guidance and methods for identifying opportunities and including them in risk discussions (e.g., strengths, weaknesses, opportunities, and threats [SWOT] analysis) Ex2: Identify stretch goals and document them Ex3: Calculate, document, and prioritize positive risks alongside negative risks | 1st Party Risk | CRI Profile v2.0: GV.RM-07 CRI Profile v2.0: GV.RM-07.01 | Conceptually new in 2.0 |
| 13 | 13 | GOVERN | Roles, Responsibilities, and Authorities | Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated | GV.RR-01 | Organizational leadership is responsible and accountable for cybersecurity risk and fosters a culture that is risk-aware, ethical, and continually improving | Ex1: Leaders (e.g., directors) agree on their roles and responsibilities in developing, implementing, and assessing the organization's cybersecurity strategy Ex2: Share leaders' expectations regarding a secure and ethical culture, especially when current events present the opportunity to highlight positive or negative examples of cybersecurity risk management Ex3: Leaders direct the CISO to maintain a comprehensive cybersecurity risk strategy and review and update it at least annually and after major events Ex4: Conduct reviews to ensure adequate authority and coordination among those responsible for managing cybersecurity risk | 1st Party Risk | SP 800-218: PO.2.3 CIS Controls v8.0: 14.1 CRI Profile v2.0: GV.RR-01 CRI Profile v2.0: GV.RR-01.01 CRI Profile v2.0: GV.RR-01.02 CRI Profile v2.0: GV.RR-01.03 CRI Profile v2.0: GV.RR-01.04 CRI Profile v2.0: GV.RR-01.05 | Conceptually new in 2.0 |
| 14 | 14 | GOVERN | Roles, Responsibilities, and Authorities | Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated | GV.RR-02 | Roles, responsibilities, and authorities related to cybersecurity risk management are established, communicated, understood, and enforced | Ex1: Document risk management roles and responsibilities in policy Ex2: Document who is responsible and accountable for cybersecurity risk management activities and how those teams and individuals are to be consulted and informed Ex3: Include cybersecurity responsibilities and performance requirements in personnel descriptions Ex4: Document performance goals for personnel with cybersecurity risk management responsibilities, and periodically measure performance to identify areas for improvement Ex5: Clearly articulate cybersecurity responsibilities within operations, risk functions, and internal audit functions | 1st Party Risk | SP 800-218: PO.2.1 CIS Controls v8.0: 14.9 CRI Profile v2.0: GV.RR-02 CRI Profile v2.0: GV.RR-02.01 CRI Profile v2.0: GV.RR-02.02 CRI Profile v2.0: GV.RR-02.03 CRI Profile v2.0: GV.RR-02.04 CRI Profile v2.0: GV.RR-02.05 CRI Profile v2.0: GV.RR-02.06 CRI Profile v2.0: GV.RR-02.07 SP 800-221A: GV.RR-1 SP 800-221A: GV.RR-2 SP 800-221A: GV.OV-2 CSF v1.1: ID.AM-6 CSF v1.1: ID.GV-2 CSF v1.1: DE.DP-1 | formerly ID.AM-06, ID.GV-02, DE.DP-01 |
| 15 | 15 | GOVERN | Roles, Responsibilities, and Authorities | Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated | GV.RR-03 | Adequate resources are allocated commensurate with the cybersecurity risk strategy, roles, responsibilities, and policies | Ex1: Conduct periodic management reviews to ensure that those given cybersecurity risk management responsibilities have the necessary authority Ex2: Identify resource allocation and investment in line with risk tolerance and response Ex3: Provide adequate and sufficient people, process, and technical resources to support the cybersecurity strategy | 1st & 3rd Party Risk | CRI Profile v2.0: GV.RR-03 CRI Profile v2.0: GV.RR-03.01 CRI Profile v2.0: GV.RR-03.02 CRI Profile v2.0: GV.RR-03.03 SP 800-221A: GV.RR-2 CSF v1.1: ID.RM-1 | |
| 16 | 16 | GOVERN | Roles, Responsibilities, and Authorities | Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated | GV.RR-04 | Cybersecurity is included in human resources practices | Ex1: Integrate cybersecurity risk management considerations into human resources processes (e.g., personnel screening, onboarding, change notification, offboarding) Ex2: Consider cybersecurity knowledge to be a positive factor in hiring, training, and retention decisions Ex3: Conduct background checks prior to onboarding new personnel for sensitive roles, and periodically repeat background checks for personnel with such roles Ex4: Define and enforce obligations for personnel to be aware of, adhere to, and uphold security policies as they relate to their roles | 1st Party Risk | CIS Controls v8.0: 6.1 CIS Controls v8.0: 6.2 CRI Profile v2.0: GV.RR-04 CRI Profile v2.0: GV.RR-04.01 CRI Profile v2.0: GV.RR-04.02 CRI Profile v2.0: GV.RR-04.03 CSF v1.1: PR.IP-11 | formerly PR.IP-11 |
| 17 | 17 | GOVERN | Policies, Processes, and Procedures | Organizational cybersecurity policy is established, communicated, and enforced | GV.PO-01 | Policy for managing cybersecurity risks is established based on organizational context, cybersecurity strategy, and priorities and is communicated and enforced | Ex1: Create, disseminate, and maintain an understandable, usable risk management policy with statements of management intent, expectations, and direction Ex2: Periodically review policy and supporting processes and procedures to ensure that they align with risk management strategy objectives and priorities, as well as the high-level direction of the cybersecurity policy Ex3: Require approval from senior management on policy Ex4: Communicate cybersecurity risk management policy and supporting processes and procedures across the organization Ex5: Require personnel to acknowledge receipt of policy when first hired, annually, and whenever policy is updated | 1st Party Risk | CRI Profile v2.0: GV.PO-01 CRI Profile v2.0: GV.PO-01.01 CRI Profile v2.0: GV.PO-01.02 CRI Profile v2.0: GV.PO-01.03 CRI Profile v2.0: GV.PO-01.04 CRI Profile v2.0: GV.PO-01.05 CRI Profile v2.0: GV.PO-01.06 CRI Profile v2.0: GV.PO-01.07 CRI Profile v2.0: GV.PO-01.08 SP 800-221A: GV.PO-1 CSF v1.1: ID.GV-1 | formerly ID.GV-01 |
| 18 | 18 | GOVERN | Policies, Processes, and Procedures | Organizational cybersecurity policy is established, communicated, and enforced | GV.PO-02 | Policy for managing cybersecurity risks is reviewed, updated, communicated, and enforced to reflect changes in requirements, threats, technology, and organizational mission | Ex1: Update policy based on periodic reviews of cybersecurity risk management results to ensure that policy and supporting processes and procedures adequately maintain risk at an acceptable level Ex2: Provide a timeline for reviewing changes to the organization's risk environment (e.g., changes in risk or in the organization's mission objectives), and communicate recommended policy updates Ex3: Update policy to reflect changes in legal and regulatory requirements Ex4: Update policy to reflect changes in technology (e.g., adoption of artificial intelligence) and changes to the business (e.g., acquisition of a new business, new contract requirements) | 1st Party Risk | CRI Profile v2.0: GV.PO-02 CRI Profile v2.0: GV.PO-02.01 SP 800-221A: GV.PO-1 CSF v1.1: ID.GV-1 | formerly ID.GV-01 |
| 19 | 19 | GOVERN | Oversight | Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy | GV.OV-01 | Cybersecurity risk management strategy outcomes are reviewed to inform and adjust strategy and direction | Ex1: Measure how well the risk management strategy and risk results have helped leaders make decisions and achieve organizational objectives Ex2: Examine whether cybersecurity risk strategies that impede operations or innovation should be adjusted | 1st Party Risk | CRI Profile v2.0: GV.OV-01 CRI Profile v2.0: GV.OV-01.01 CRI Profile v2.0: GV.OV-01.02 CRI Profile v2.0: GV.OV-01.03 SP 800-221A: GV.AD-3 | Conceptually new in 2.0 |
| 20 | 20 | GOVERN | Oversight | Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy | GV.OV-02 | The cybersecurity risk management strategy is reviewed and adjusted to ensure coverage of organizational requirements and risks | Ex1: Review audit findings to confirm whether the existing cybersecurity strategy has ensured compliance with internal and external requirements Ex2: Review the performance oversight of those in cybersecurity-related roles to determine whether policy changes are necessary Ex3: Review strategy in light of cybersecurity incidents | 1st Party Risk | CRI Profile v2.0: GV.OV-02 CRI Profile v2.0: GV.OV-02.01 CRI Profile v2.0: GV.OV-02.02 SP 800-221A: GV.AD-2 SP 800-221A: GV.AD-3 SP 800-221A: MA.RM-8 | Conceptually new in 2.0 |
| 21 | 21 | GOVERN | Oversight | Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy | GV.OV-03 | Organizational cybersecurity risk management performance is evaluated and reviewed for adjustments needed | Ex1: Review key performance indicators (KPIs) to ensure that organization-wide policies and procedures achieve objectives Ex2: Review key risk indicators (KRIs) to identify risks the organization faces, including likelihood and potential impact Ex3: Collect and communicate metrics on cybersecurity risk management with senior leadership | 1st Party Risk | CRI Profile v2.0: GV.OV-03 CRI Profile v2.0: GV.OV-03.01 CRI Profile v2.0: GV.OV-03.02 SP 800-221A: GV.OV-2 SP 800-221A: MA.RM-2 | Conceptually new in 2.0 |
| 22 | 22 | GOVERN | Cybersecurity Supply Chain Risk Management | Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders | GV.SC-01 | A cybersecurity supply chain risk management program, strategy, objectives, policies, and processes are established and agreed to by organizational stakeholders | Ex1: Establish a strategy that expresses the objectives of the cybersecurity supply chain risk management program Ex2: Develop the cybersecurity supply chain risk management program, including a plan (with milestones), policies, and procedures that guide implementation and improvement of the program, and share the policies and procedures with the organizational stakeholders Ex3: Develop and implement program processes based on the strategy, objectives, policies, and procedures that are agreed upon and performed by the organizational stakeholders Ex4: Establish a cross-organizational mechanism that ensures alignment between functions that contribute to cybersecurity supply chain risk management, such as cybersecurity, IT, operations, legal, human resources, and engineering | 3rd Party Risk | CIS Controls v8.0: 15.2 CRI Profile v2.0: GV.SC-01 CRI Profile v2.0: GV.SC-01.01 CRI Profile v2.0: GV.SC-01.02 SP 800-221A: GV.PO-1 CSF v1.1: ID.SC-1 | |
| 23 | 23 | GOVERN | Cybersecurity Supply Chain Risk Management | Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders | GV.SC-02 | Cybersecurity roles and responsibilities for suppliers, customers, and partners are established, communicated, and coordinated internally and externally | Ex1: Identify one or more specific roles or positions that will be responsible and accountable for planning, resourcing, and executing cybersecurity supply chain risk management activities Ex2: Document cybersecurity supply chain risk management roles and responsibilities in policy Ex3: Create responsibility matrixes to document who will be responsible and accountable for cybersecurity supply chain risk management activities and how those teams and individuals will be consulted and informed Ex4: Include cybersecurity supply chain risk management responsibilities and performance requirements in personnel descriptions to ensure clarity and improve accountability Ex5: Document performance goals for personnel with cybersecurity risk management-specific responsibilities, and periodically measure them to demonstrate and improve performance Ex6: Develop roles and responsibilities for suppliers, customers, and business partners to address shared responsibilities for applicable cybersecurity risks, and integrate them into organizational policies and applicable third-party agreements Ex7: Internally communicate cybersecurity supply chain risk management roles and responsibilities for third parties Ex8: Establish rules and protocols for information sharing and reporting processes between the organization and its suppliers | 3rd Party Risk | SP 800-218: PO.2.1 CIS Controls v8.0: 15.4 CRI Profile v2.0: GV.SC-02 CRI Profile v2.0: GV.SC-02.01 SP 800-221A: GV.RR-1 SP 800-221A: GV.RR-2 CSF v1.1: ID.AM-6 | |
| 24 | 24 | GOVERN | Cybersecurity Supply Chain Risk Management | Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders | GV.SC-03 | Cybersecurity supply chain risk management is integrated into cybersecurity and enterprise risk management, risk assessment, and improvement processes | Ex1: Identify areas of alignment and overlap with cybersecurity and enterprise risk management Ex2: Establish integrated control sets for cybersecurity risk management and cybersecurity supply chain risk management Ex3: Integrate cybersecurity supply chain risk management into improvement processes Ex4: Escalate material cybersecurity risks in supply chains to senior management, and address them at the enterprise risk management level | 3rd Party Risk | SP 800-218: PW.4.1 CRI Profile v2.0: GV.SC-03 CRI Profile v2.0: GV.SC-03.01 SP 800-221A: GV.CT-2 SP 800-221A: GV.CT-3 CSF v1.1: ID.SC-2 | Conceptually new in 2.0 |
| 25 | 25 | GOVERN | Cybersecurity Supply Chain Risk Management | Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders | GV.SC-04 | Suppliers are known and prioritized by criticality | Ex1: Develop criteria for supplier criticality based on, for example, the sensitivity of data processed or possessed by suppliers, the degree of access to the organization's systems, and the importance of the products or services to the organization's mission Ex2: Keep a record of all suppliers, and prioritize suppliers based on the criticality criteria | 3rd Party Risk | CIS Controls v8.0: 15.1 CIS Controls v8.0: 15.3 CRI Profile v2.0: GV.SC-04 CRI Profile v2.0: GV.SC-04.01 SP 800-221A: GV.CT-2 SP 800-221A: GV.CT-3 CSF v1.1: ID.SC-2 | |
| Function | Category | Risk Applicability |
