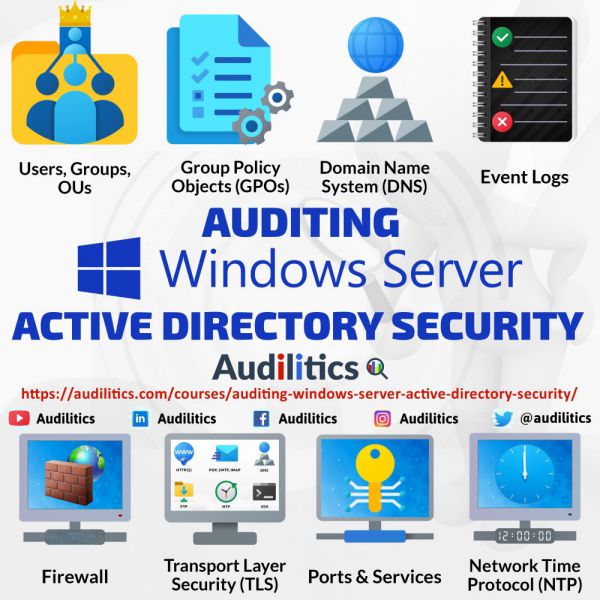
Roles and Responsibilities for Information Security and Risk Management
Table of Contents ToggleChief Executive Officer (CEO)Chief Information Officer (CIO)Chief Information Security Officer (CISO)Chief Risk Officer (CRO)Data Privacy Officer (DPO)Information Security ArchitectInformation Security Control AssessorInformation OwnerSystem...
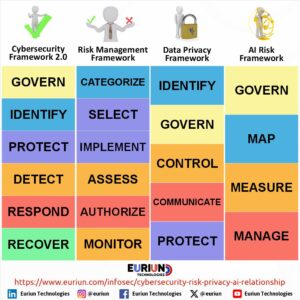
Enterprise Architecture Security Design Principles
Test your knowledge Zero Trust Security (Identity, Device, Network, OS, Database, Application, Data) The implementation of a Zero Trust Security Model to cover all enterprise assets, resources (end users, applications and other non-human entities that request...
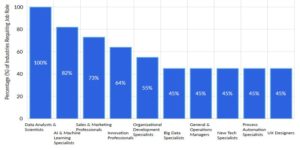
Information Security Threats to Watch Out For In 2019
The highlights from the 2019 Symantec Internet Security Threat Report showcases the latest trends in cyber security attacks, including ransomware, formjacking, and cloud security. Incidents of formjacking (The use of malicious JavaScript code to steal credit card...
Top Mobile Security Threats To Watch Out For In 2019
The highlights from the Symantec Internet Security Threat Report for 2018 showed the overall number of mobile malware infections reduced in 2018 but with a rapid increase in the number of mobile devices ransomware infections, up by a third when compared to 2017. The...